$50 million for our community
ACESO Network is beneficial to everyone involved, both regular users and cybersecurity specialists. For regular users, it’s cheap but effective security, for specialists — a way to earn substantial income by helping malware-infected users. It may be confusing at first as to how researchers and malware analysts earn tokens, and how much income will they actually get, but this report should make everything much clearer.
It is important to note that while certain skills are required, essentially anyone could become part of ACESO. The role of a researcher will be to provide malware samples, which he/she may encounter while browsing the Internet or purposely looking for them. Malware analysts, on the other hand, will provide fixes for malware issues. Analysts are required to have knowledge and experience in the field as otherwise they will not be able to help. However, ACESO will provide guidelines and resources for those interested in gaining knowledge in cybersecurity. So what exactly are the roles of researchers and malware analysts, and how will they earn money?
Researchers
Some users hunt for malware samples for fun or for work, some encounter malware regularly because of their risky browsing habits. Whatever the case may be, we want to use that to create a significant database of malware, and in exchange for their help, reward contributors.
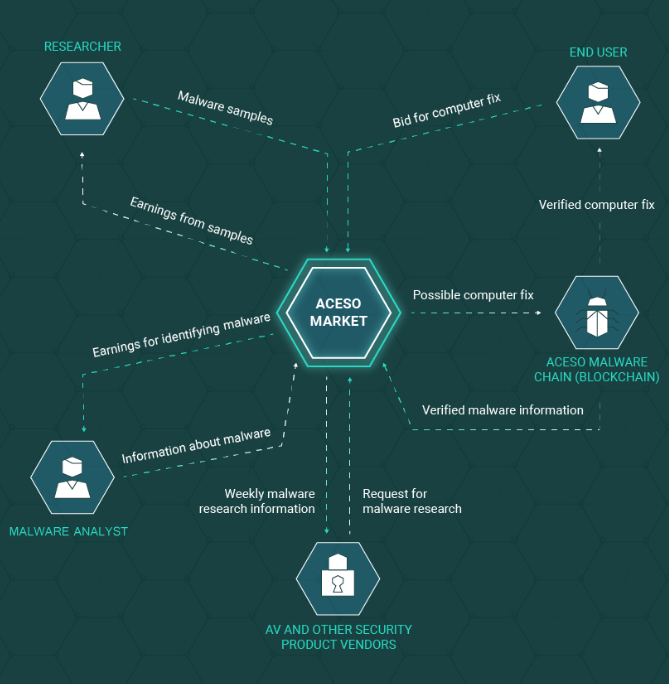
Researchers will upload potential malware samples or infected system screenshots to the ACESO database. The submitted samples will be analysed, and it will be determined whether they are malware. When a submitted malware sample is used by a malware analyst to develop a fix, the researcher who provided it will get 30% of the rewards offered for that fix. This means that not all submitted samples are rewarded, only those that match a fix request.
A special platform will be created for ACESO researchers to upload samples and system screenshots to. Researchers will be able to scan their computers with special software when they notice unusual computer behaviour. The information acquired from the scan would be uploaded onto the ACESO Market. The information would then be analysed for signs of malware.
The method of uploading samples or system screenshots would be made as simple and quick as possible, as would the reward distribution. The easier the process is, the more people will likely join our community, which will make it bigger and more profitable for all.
We should note, however, that we do not encourage purposely infecting computers for inexperienced users as it could result in serious damage.
Malware Analysts
A lot of skilful cybersecurity experts help out in various forums for free. They spend their valuable time helping infected users deal with malware infections but often do not even get a ‘thank you’ in return. Their skills are invaluable and we want to provide experts the opportunity to put those skills to good use and earn money.
Malware analysts are one of the most integral parts of ACESO as they are the ones who provide fixes for users. Thus, it makes sense that they are the ones who will benefit the most. For one fix, they will get 60% of all offered rewards. Because malware analysts will create fixes for malware, they do need to have special skills and knowledge. But as we’ve mentioned before, less experienced users will have the option of using ACESO provided instructions and guidelines to help them gain more skill and learn how everything is done.
Malware analysts will have the option of picking up requests from users. Infected users will even be able to pick particular analysts to fix their computers. Once a request is taken, the analyst is tasked to create a working fix. How they do it is up to them. They receive information from the infection computer, and may use samples provided by researchers, or they may find them themselves. When they develop a working fix, they get rewarded 60% of the offered reward.
How much money will researchers and analysts actually earn?
What makes ACESO different from other cybersecurity vendors is that we give back to the community and only keep small percentages of revenue. Most companies earn a lot of money and keep their profits to themselves. For example, Kaspersky earned almost $700 million in revenue in 2017, while Symantec had a revenue of $4 billion. However, what we want to do is different. We want to reward cybersecurity specialists for their hard work, while at the same time making cybersecurity cheaper for regular computer users.
One fix costs $1, so 30% or 60% of a dollar is not exactly great money. However, generally, when malware strikes, it’s not just one person that ends up infected. There are usually thousands of computers corrupted with the same malware. If those thousands of users use ACESO, they would all have to pay $1 in order to get the fix. If the same fix applies to all of them, all their payments would be put into a pot and then distributed to those who contributed to developing that fix. Researchers get 30%, malware analysts get 60% and ACESO takes only 10%.
We have estimated that in the first year, the overall income earned by malware researchers and analysts (community earnings) will be approximately $2.1 million. In year two, we expect that the sum will reach $3.5 million and will steadily increase over the years, with $7.3 million in year three, $14.8 million in year four, and $25.2 million in year five. All together it should be more than $50 million in 5 years!
If you become part of our community, whether as a researcher or a malware analyst, your skills will not go to waste. They will not only be appreciated but also rewarded. ACESO aims to create a safer cyber world, and you could be part of that. If you want to find out more about ACESO Network and how you could join, you can visit our website to access resources or read the whitepaper for a more detailed explanation.